TL;DR
Kubernetes has experienced tremendous amounts of growth in terms of popularity. Over 4,000 attendees of Kubecon + CloudNativeCon was a reflection of this growth.
At this year’s conference, there was a lot of talk about different types of service mesh, automated testing tools, deployment strategies and a ton of products that now offer Kubernetes-specific integration. There are also new products that are meant to replace parts of Kubernetes with enhanced or use-case specific components.
Community Growth
KubeCon + CloudNativeCon started with Dan Kohn (Executive Director of the Cloud Native Computing Foundation) dropping some numbers with regards to community growth.
One of the metrics that stood out to me was the growth in the number of attendees for KubeCon + CloudNativeCon over the past couple of years.
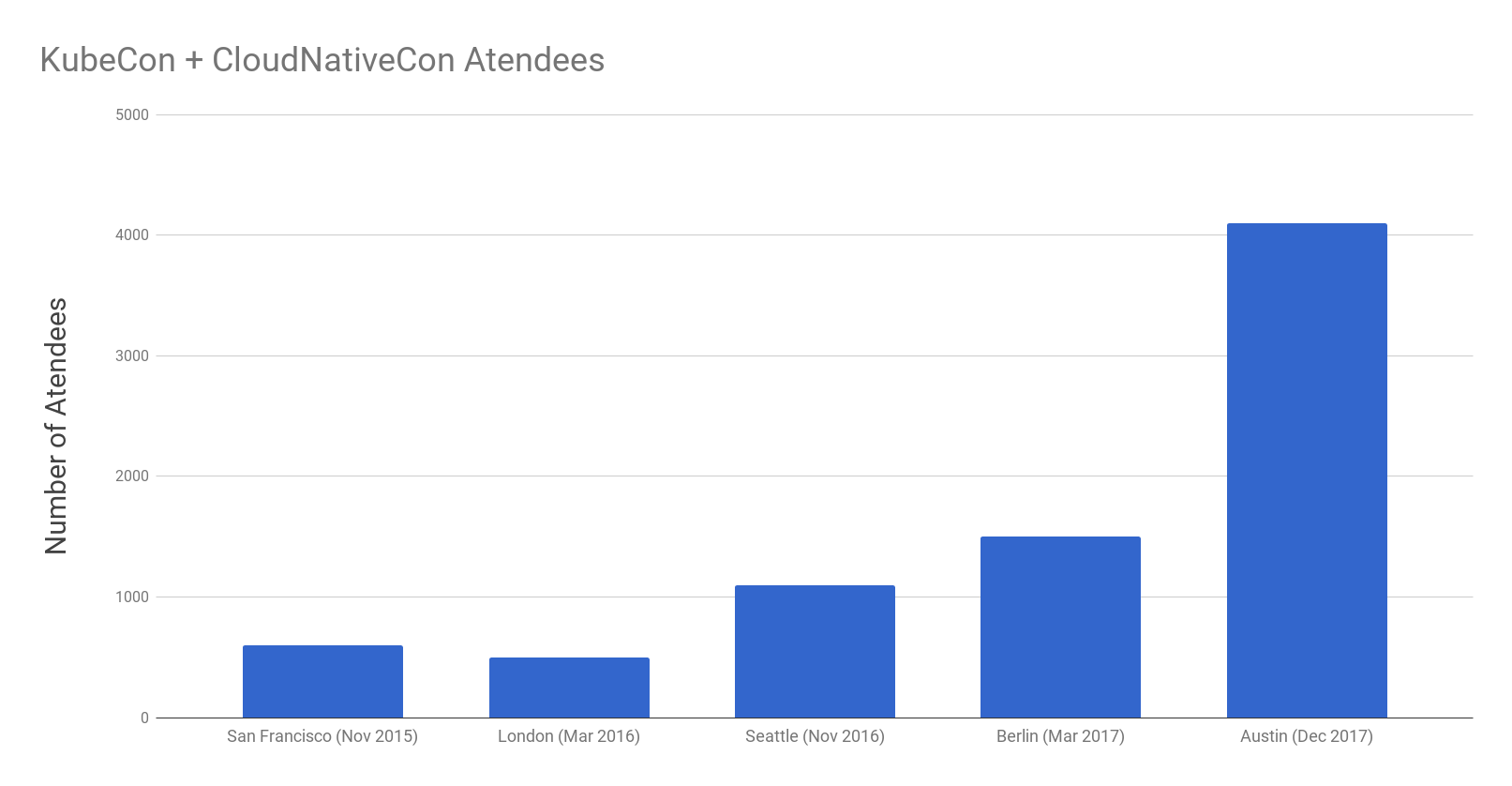
The conference this year attracted over 4,000 attendees compared to just over 1,000 attendees at last year’s North American conference in Seattle.
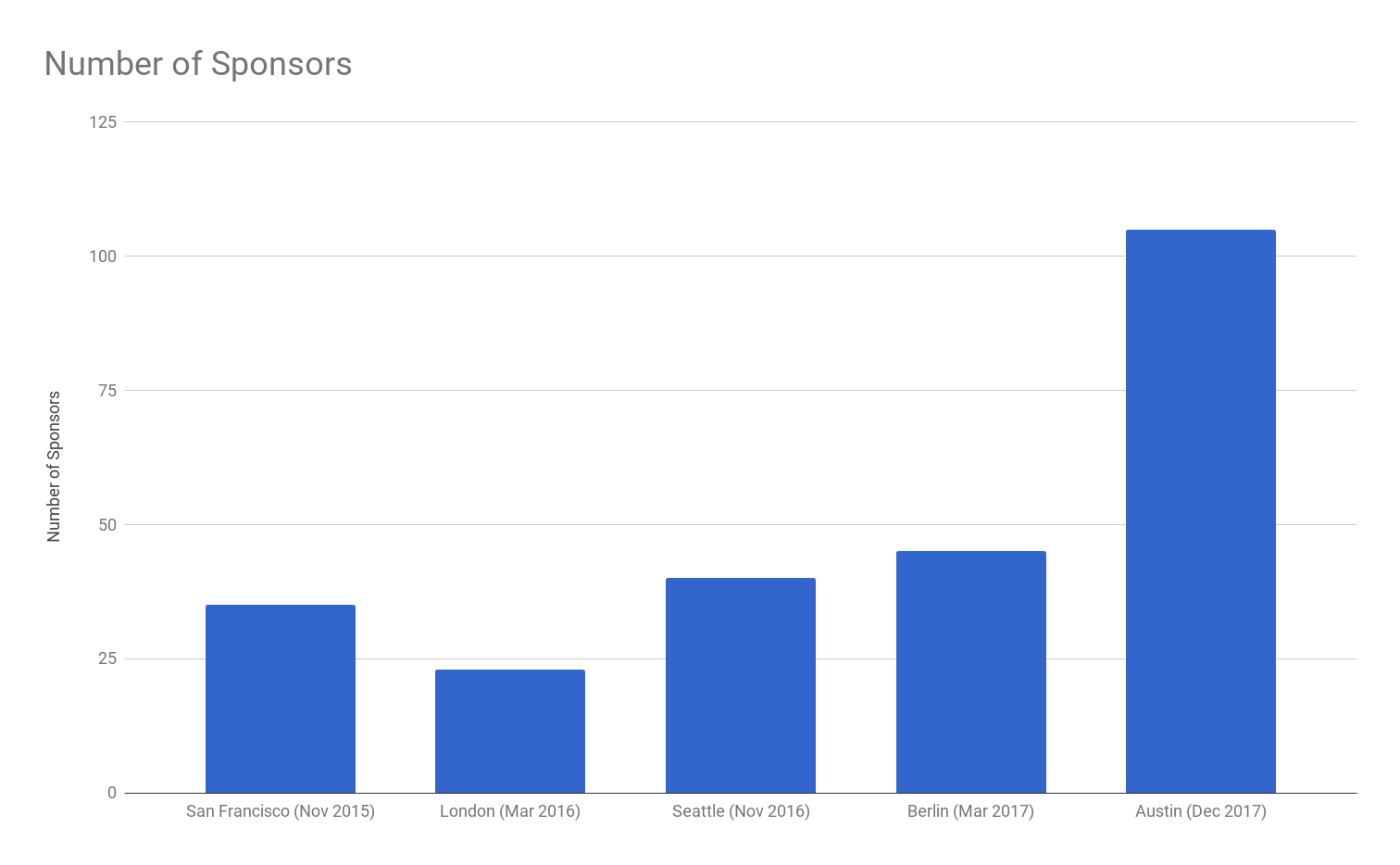
The other metric that was quite apparent throughout the conference was the number of sponsors. There were a ton of products targeting companies who were deploying using Kubernetes. The number of sponsors more than doubled in a year.
Kubernetes & Service Mesh
There was a lot of talk about different types of service mesh for Kubernetes. One that stood out at multiple talks was Istio. This service mesh offers a broad range of enhancement to service discovery, routing and overall security.
Canary Testing
One of the best demos that I saw was prepared by Brian Redmond (Azure Architect at Microsoft) who swears that his last name was Redmond prior to working at Microsoft.
Brian used Istio’s advanced routing capabilities to show us how we could do a canary deployment in a microservices architecture on Kuberrnetes. His demo included a CI/CD pipeline built with Brigade. The full tutorial can be found on his blog.
Security with Istio-Auth
I was amazed to find out that Istio will offer pod-to-pod TLS termination with zero changes to code. It does this by injecting it’s Envoy container into pods. This container transparently intercepts and proxies HTTP, gRPC, and TCP traffic.
Credits: Spike Curtis (Tigera) & Dan Berg (IBM)
Istio will also handle key and certificate generation, deployment, rotation, and revocation. It will also take care of egress policy. This means that if malicious code is injected into a service, the perpetrator won’t be able to communicate with an external source that is not white-listed with Istio.
Credits: Spike Curtis (Tigera) & Dan Berg (IBM)
Conference Sponsors
There was no shortage of sponsors in the sponsors section. From startups to big enterprise, everyone wants to get in on Kubernetes one way or another.
Here’s a list of sponsors that stood out to me:
- RedHat’s OpenShift is a managed Kubernetes solution – if you want to experiment with Kubrnetes, they’re offering a free cluster that will host up to 4 pods
- LogDNA has an incredibly easy-to-setup logging solution for Kubernetes – I literally set it up by copying and pasting two commands
- HashiCorp’s Vault is the best solution that I’ve seen for managing secrets across an organization – the best part? they have a Kubernetes plugin and are working closely with the community to make it a tight integration
Thanks for reading. Let me know if there was anything that stood out to you!